Set Up VPC Peering between Amazon Virtual Private Clouds (VPCs)
Lab Overview
In this Lab, you will make strides in migrating an on-premises application into the AWS cloud. You will configure the networking between two VPCs, one for the frontend web tier and one for the backend API tier. As part of a real-world scenario, you will complete design requirements and debug network issues.
Lab Objectives
Upon completion of this Lab you will be able to:
- Connect VPCs using peering connections
- Use custom DNS names in your networks using Amazon Route 53 private hosted zones
- Diagnose and debug network issues using VPC flow logs
Lab Prerequisites
You should be familiar with the following:
- AWS networking concepts including VPCs, subnets, internet gateways, security groups, and route tables
- AWS compute concepts including EC2 instances, load balancers, Auto Scaling groups, and launch configurations
Lab Environment
Before completing the Lab instructions, the environment will look as follows:
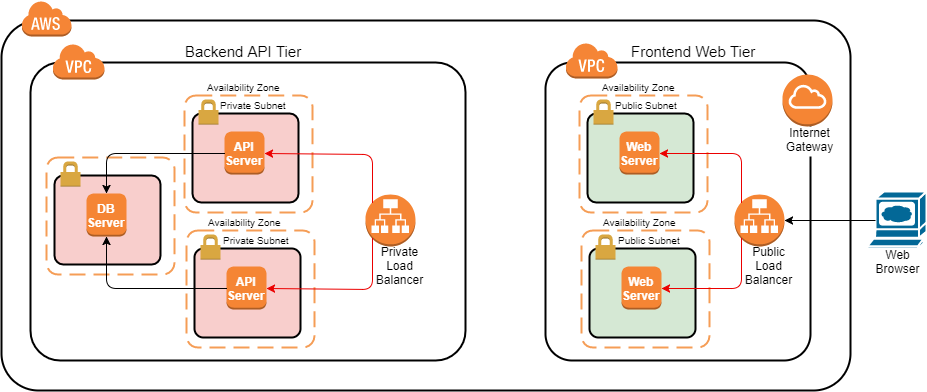
After completing the Lab instructions, the environment should look similar to:
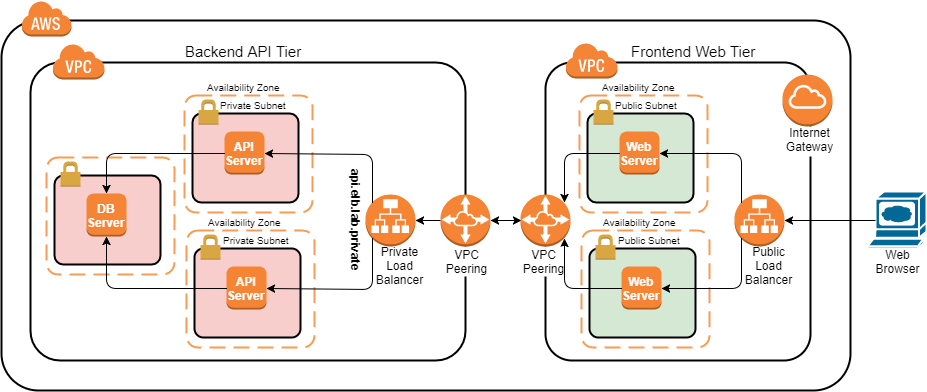
Updates
December 7th, 2023 - Resolved an issue that caused the lab to fail to setup on rare occasions
October 10th, 2023 - Resolved Node.js issue
March 19th, 2023 - Updated instructions and screenshots to reflect latest UI
May 31st, 2022 - Corrected permissions issue regarding flow log creation
September 16, 2021 - Replaced screenshots for peer connecting request and modifying route table
April 23rd, 2021 - Updated load balancer screenshots to reflect the latest user interface
March 10th, 2021 - Updated flow log screenshots and instructions to reflect the latest user-interface changes
January 10th, 2019 - Added a validation Lab Step to check the work you perform in the Lab
Logan has been involved in software development and research since 2007 and has been in the cloud since 2012. He is an AWS Certified DevOps Engineer - Professional, AWS Certified Solutions Architect - Professional, Microsoft Certified Azure Solutions Architect Expert, MCSE: Cloud Platform and Infrastructure, Google Cloud Certified Associate Cloud Engineer, Certified Kubernetes Security Specialist (CKS), Certified Kubernetes Administrator (CKA), Certified Kubernetes Application Developer (CKAD), and Certified OpenStack Administrator (COA). He earned his Ph.D. studying design automation and enjoys all things tech.