Manage Access to Azure With Role-Based Access Control
Lab Overview
The 'principle of least privilege' states that security of resources is improved when workers only have the access they need to perform their job roles. Azure provides fine-grained role-based access control (RBAC) mechanisms to secure your cloud environment. In this Lab, you will follow the principle of least privilege for users as you manage access to Azure with RBAC. You will use Azure PowerShell to create a custom role, learn how to assign roles to users, and get tips on how to define your own custom roles.
Lab Objectives
Upon completion of this Lab you will be able to:
- Create custom roles using Azure PowerShell
- Investigate user access control errors
- Develop custom roles using the Azure Portal and PowerShell
Lab Prerequisites
You should be familiar with:
- Basic Azure resources, such as Subnets, Virtual Machines, and Network Security Groups
Lab Environment
Before completing the Lab instructions, the environment will look as follows:
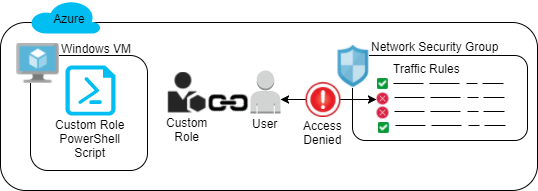
After completing the Lab instructions, the environment should look similar to:
Updates
May 9th, 2023 - Updated outdated screenshot
January 25th, 2022 - Modified some cmdlets due to changes resulting from the cmdlets using Microsoft Graph instead of Azure AD Graph
September 22nd, 2021 - Updated screenshots and instructions to reflect the latest UI experience
February 20th, 2020 - Added a validation check to check the work performed in the lab
February 19th, 2020 - Updated lab to use the Az PowerShell module
December 16th, 2019 - Updated VM to Windows 2019 Datacenter and resolved an issue that caused the bootstrap script to fail in one case
October 22nd, 2019 - Improved instructions related to first loading the lab PowerShell script
Logan has been involved in software development and research since 2007 and has been in the cloud since 2012. He is an AWS Certified DevOps Engineer - Professional, AWS Certified Solutions Architect - Professional, Microsoft Certified Azure Solutions Architect Expert, MCSE: Cloud Platform and Infrastructure, Google Cloud Certified Associate Cloud Engineer, Certified Kubernetes Security Specialist (CKS), Certified Kubernetes Administrator (CKA), Certified Kubernetes Application Developer (CKAD), and Certified OpenStack Administrator (COA). He earned his Ph.D. studying design automation and enjoys all things tech.