Black Friday & Cyber Monday coming at us fast, and like we say every year, they are going to be bigger than ever. There are more e-commerce stores than ever before, meaning competition is fierce, and with a rocky economic landscape, consumers will be savvier than ever. So you need to focus on attracting customers before your competitors so that when shoppers are ready to buy—your brand is the one that is top of mind.
Ad prices are notoriously high and variable during the holiday season. That’s why building a strong, engaged email list ahead of time is the key. You’ll be in a perfect position for your marketing campaigns without paying through the roof for them.
In this blog, we’re going to cover how to run A/B tests to learn what will work best for you, your brand, and your customers. This will help grow your list between now and the holidays, so you can head into the season with confidence.
Before The Holiday: Test & Learn
The best time for brands to learn what will work best for them and their customers is before the retail holidays begin. Best practices are a great place to start, but you should run tests and experiments to find out what’s most impactful for your target audience and brand.
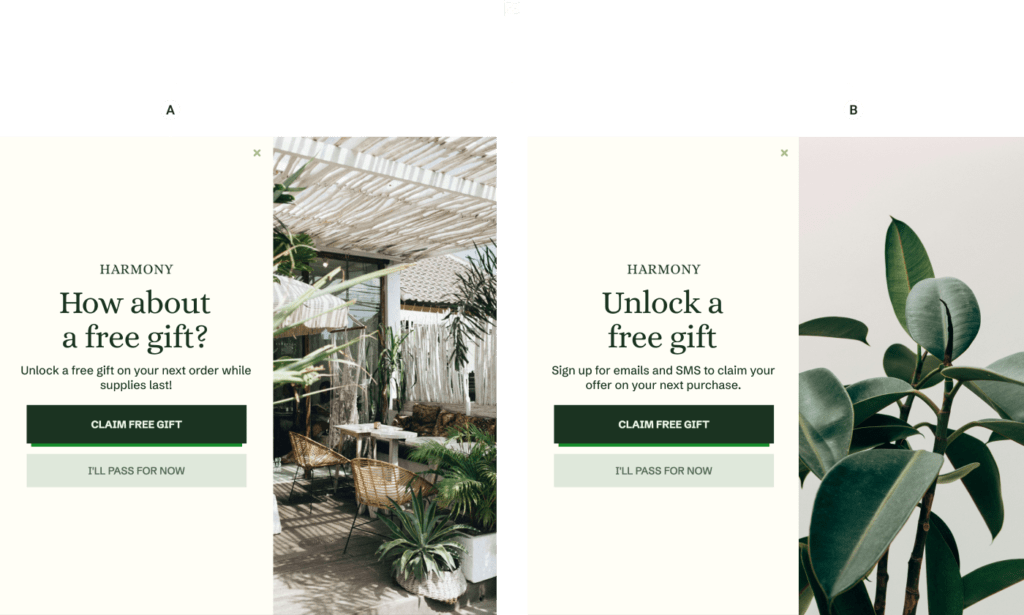
A/B testing is the most effective way to empirically find the most impactful approach for almost any marketing campaign. This is where 50% of customers see one version, Version A, and 50% see another, Version B, and the winner is delivered to your broader audience. The great thing about A/B testing is that you can stack your results on top of one another and generate significant compounding growth.
Most marketing tools, including Justuno, have built-in A/B testing to run your experiments. These let you run tests on targeting, messaging, offers, graphics, timing, and more marketing variables. So where do you start? I suggest you start with the marketing funnel, AKA the customer journey and specifically the stages: Awareness, Consideration, Purchase, and Post-Purchase.
Top Of The Funnel
The top of the funnel is the stage where customers are aware of a need they’re trying to satisfy and go out searching. This is where they’ll have their first impression of your brand. Often on an external platform such as Instagram, Facebook, Search, blogs, and reviews. The top of the funnel is a great place to start your testing. Since the number of eyeballs is the largest, you will likely see results in just a few days of testing.
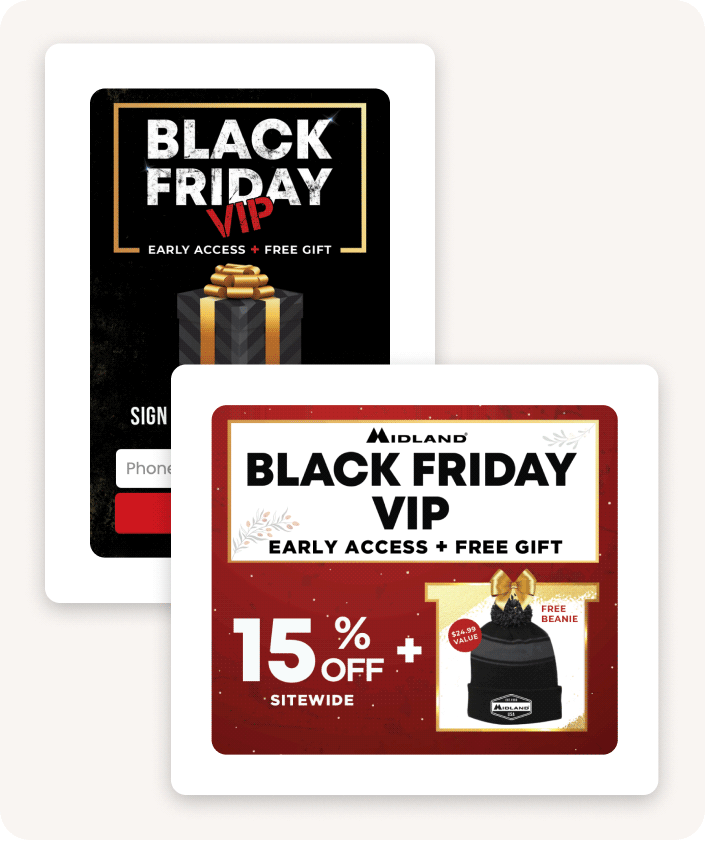
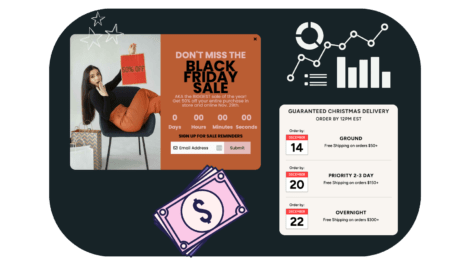
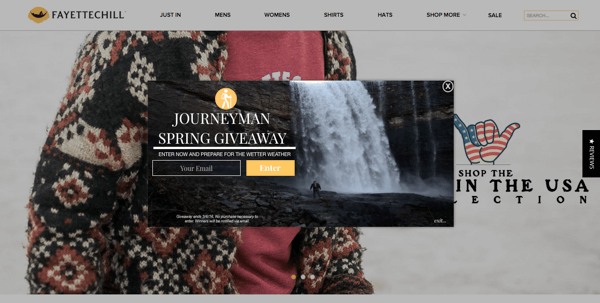
This will be especially important in the months (and weeks) leading up to the holiday sales because this is the ideal phrase for list growth. People are expecting big sales and subscribing to emails in anticipation or just starting their shopping and coming across your site. Either way, the more subscribers you have pre-holidays, the less you’ll spend on acquisition later on.
Top-of-funnel tests include:
- Ad copy
- Landing pages
- Signup offer
- Popup design
We also recommend focusing on not just collecting emails from these new subscribers but additional zero-party data as well to inform your holiday marketing.
Pro Tip: Our guide, Zero & First-Party Data for The Holidays, outlines strategies for collection & implementation throughout the customer journey.
Middle of The Funnel
The middle of the funnel, the consideration stage, is when customers are considering your brand/product against their needs and your competitors.
The data from these tests will help you learn techniques and messaging that resonate most with your target audience and move them through the funnel.
Middle-of-funnel tests include:
- Upsell popups
- Automated nurture emails
- Automated product education emails
- Newsletter send time
- Newsletter send day
- Newsletter frequency
- Newsletter content types
Bottom of The Funnel
A customer making a purchase isn’t the end of the journey; it’s the start of two new ones: referring friends through advocacy and increasing customer lifetime value with repeat purchases and upsells.
If you have a strong bottom-of-the-funnel strategy during your sales period, you will convert one-time, sales-focused customers into long-term repeat customers and brand advocates.
Bottom-of-funnel tests include:
- New customer nurture emails
- Product education/demonstration emails
- Review requests
- Social share requests
- Referral programs

How To Run Tests
Learning from A/B tests is simple if you follow a few basic rules to ensure the results you see are valid and apply them to compound your growth.
Firstly, run only one test for each stage of the funnel at a time. For example, if you are running A/B tests on your ad copy, resist running tests on your landing page at the same time. Running A/B tests at the same time would mean you can’t be certain which element and variation are causing the change. Test the ad copy this week and the landing page afterward.
Secondly, control for other variables as much as possible. Rather than testing Version A one week and Version B the next, run them at the same time wherever possible to control for outside influences between the weeks. Use your testing software to randomize which customers receive each version so audience differences are controlled for. Otherwise, differences in your results could be due to fundamentally different audiences for each variation, not the variation itself.
Next, make sure that you have enough data. If you see a large difference in conversions from only a few visitors, it’s likely that random variations from the small sample are causing the differences. Random changes will be less influential if you wait a few days, and the results will be more definitive. More time and visitors are always ideal when it comes to running A/B tests: when in doubt, let it run a bit longer!
Finally, try to set out to learn things that will teach you long-lasting lessons that can be built on in the future. For example, when you design a pop-up, try big-picture elements first, like a percentage offer vs a dollar amount. That way, you will know the foundation for future promotions and can test other elements like center vs full-screen.
When A/B testing email designs pre-holiday, don’t just try one design vs. another; try a long-form email design vs. a similar short one. This will help you learn what your target customers respond to and lets you adjust your strategies going forward. Incremental testing and changes can lead to big improvements over time!
It’s an exciting time of the year, and with these tips, you’re sure to turn this holiday season into a customer acquisition powerhouse.
Want more holiday resources? Check out our BFCM page with all the content you need to make this holiday season your best one yet!