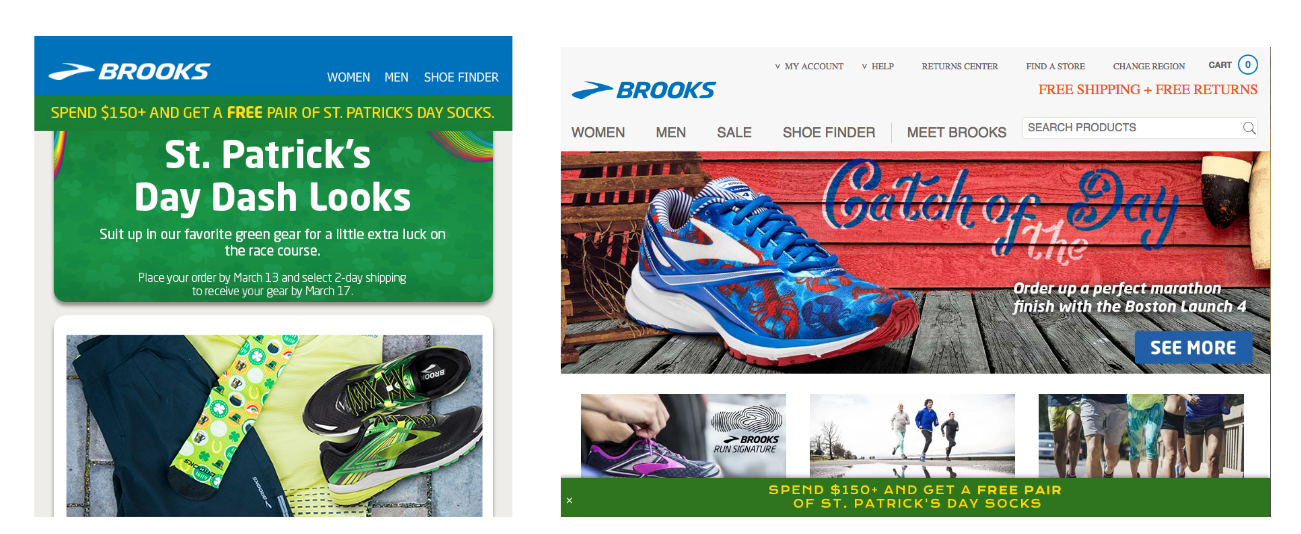
November is a busy month for marketers; the madness of Black Friday/Cyber Monday has been looming for ages, and it’s finally here. But November has other sales and marketing opportunities to take advantage of, so you’re not putting all your conversion eggs in one basket, so to speak.
November Calendar
- November 1: Diwali
- November 3: Daylight Savings ends
- November 5: Election Day (US)
- November 11: Singles Day (China)
- November 11: Veterans Day (US)
- November 27: Green Wednesday
- No Shave November/Movember
—-Cyber Week—-
- November 28: Thanksgiving
- November 29: Black Friday
- November 30: Small Business Saturday
- December 2: Cyber Monday
- December 3: Giving Tuesday
November kicks off with Diwali, the most celebrated festival in India, not to mention a huge celebration around the world, on November 1st. Shopping and gift-giving are a huge part of Diwali traditions, so make sure to offer options for customers looking to shop or celebrate
That’s quickly followed by the end of Daylight Savings, also known as Fall Back, on the first Sunday of the month (November 3rd) which gives us an extra hour of sleep. It’s the good time change :)
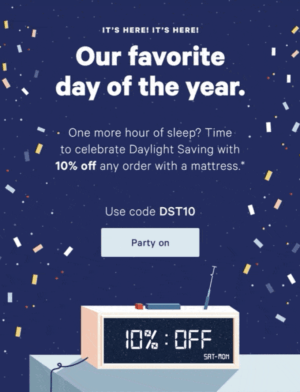
Run a campaign that day featuring “an extra hour to shop” or leaning into the cozy, fall vibes that we all associate with it.
Just a few days later, the US has Election Day, which varies from year to year, and while most of us only focus on elections when it’s a Presidential race like this year’s—there are votes cast every year at this time. Encourage consumers to get out and vote with rewards for participating in their local elections.
After that comes 11/11, also known as Singles Day in China. This is the single biggest and busiest shopping day of the year: more products are bought in 24 hours than some countries make in an entire year. Singles Day is a celebration of yourself, a sort of anti-Valentine’s Day treat-yo-self holiday.
Popularized by Chinese retailer Alibaba, it’s taken on a life of its own and become a cultural phenomenon. If you’re selling in China, run a dedicated Singles Day campaign via email and on your website featuring steep discounts. For US brands looking to get in on the fun—lean into the treat-yo self aspect and encourage shoppers to get themselves something before they have to think of what to gift everyone else this season.
November 11th is also Veterans Day in the US, and for those observing it, it is a somber occasion. Obviously, that’s the opposite of the messaging for Singles Day – make sure not to do both and be aware of your audience.
November 27th is Green Wednesday, a shopping holiday coined by the Cannabis industry in 2017. It’s the Wednesday before Thanksgiving and is associated with a surge in sales online and in dispensaries. Green Wednesday is the ultimate day for Cannabis brands to run a Black Friday-esque sale a little early and capitalize on this growing trend!
Pro Tip: If you’re a Cannabis brand, check out SpringBig the industry-leading marketing platform for regulated industries.
The entire month of November is known as ‘No Shave November’ or ‘Movember’, which is meant to bring awareness to men’s health issues. It’s popular to grow out your mustache or bread during this time, with many groups raising money through contests and games. If it aligns with your brand image, this is a great opportunity to do some cause-based marketing and connect with your customers. Men’s brands, from clothing to skincare, can get involved with things like mustache contests, donations to various charities, and more.
Then, rounding out the month is the infamous cyber week, starting with Thanksgiving on November 28th and running through Giving Tuesday on December 3rd.
There’s plenty of content around that talks about strategies to use during the holidays, so we’ll keep this summary short and sweet:
Thanksgiving
Run a VIP/early-access campaign to get shoppers in the door early. There are plenty of people browsing Instagram while their pies bake, or they’re avoiding the family football game.
Black Friday
This is one of the two biggest days of the entire weekend, so run your big sale, keep everything unlocked, and most importantly, keep it simple.

Small Business Saturday
Really lean into the why behind your brand for this day; consumers like to support small businesses, especially if they have a strong connection to it. With a strong connection, they’re that much more likely to check out.
Bonus points if you have a brick-and-mortar store to drive foot traffic to for local shoppers.
Cyber Monday
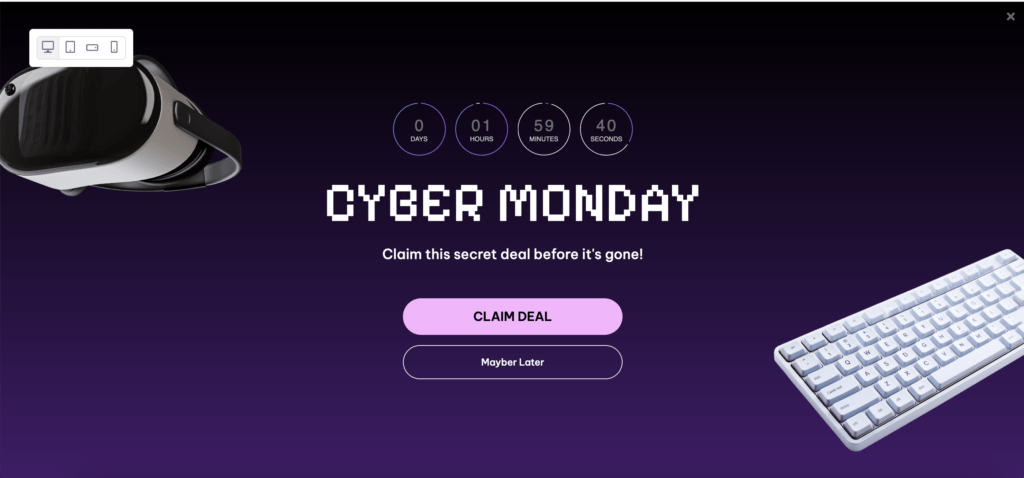
Run your second big sale (or switch up the offer from Black Friday), keep everything unlocked, keep it simple, and use countdown timers to make sure that customers know this is their last chance to save big. You can also lean into the fact that now that Thanksgiving is over–it’s Christmas time! Start sending emails with content centered around that to drive consumers back to your site.
Giving Tuesday
Use the final day of Cyber Week to highlight causes your brand supports. It’s important that this is genuine and not a one-off campaign. Consumers know when something is fake, and it’s a major turn-off. If this isn’t something your brand does year-round, then this isn’t the holiday for you! For those like our customer, Sheets & Giggles, who plants two trees for every tree harvested already, they could double that or create some other kind of increased giving campaign to incentivize shoppers on Giving Tuesday.

November is the Super Bowl of e-commerce, but it’s not all about Cyber Week. There are a few other opportunities to stand out this month beyond the BFCM craze. Not to mention there’s plenty of time left in December to drive holiday sales.
Looking for more holiday content? Check out our BFCM corner for all things holiday content and our 2024 marketing calendar to see other sales opportunities to plan for.
Want some extra help this holiday season? We offer a holiday package for retailers who just want short-term extra hands to support them during the busy season. Learn more here and book a call to reserve your spot!