Would you like fries with that?
Acquiring new customers is more expensive than keeping your current ones. Since you’ve already established trust and built a relationship with existing customers, they’re more likely to try new products and spend more per order than new buyers.
Overview
However, the first step of nurturing existing customers into higher Average Order Values (AOV) is to first convert visitors into customers. By investing more into converting your existing website traffic, you will create more repeat customers and ultimately reduce the money spent on attracting new shoppers.
One way to increase existing customer AOV and convert more new customers is with upselling and cross-selling promotions. These promotions are designed specifically to improve the customer experience by offering visitors more of what they want, ultimately boosting AOV.
Justuno has two options for implementing upselling and cross-selling promotions on your site: either using basic targeting rules available on all plans or AI-powered features exclusive to Justuno Plus customers.
On our Basic plans, you can use targeting rules to specify which visitors should see promotions using parameters like previous URLs visited, current cart total, or contents.
For those on Justuno Plus, our AI-powered upsell and cross-selling features automatically curate personally relevant recommendations based on site behavior, cart contents, purchase history, and more. These features work in tandem with your product catalog and store information to continuously learn and optimize your site experience.
Details
Take for example Natural Solutions, a CBD shop who wants to increase their average order value and optimize their conversion rate. As a CBD retailer, they fall under similar restrictions as alcohol and tobacco companies and aren’t allowed to use paid Google ads to drive traffic to their site. Therefore, it’s incredibly important that Natural Solutions make the absolute most out of their existing traffic, without harming any of their organic traffic rankings.
For Natural Solutions, cross-selling was the best fit for their brand since their products are relatively equal in price point and using them in conjunction tends to boost customer satisfaction.
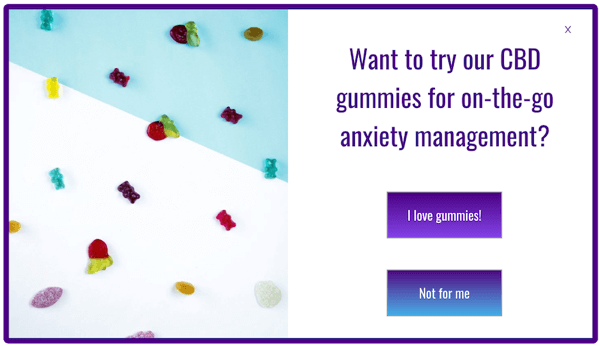
Natural Solutions ran pop-ups targeting visitors who added a starter kit to their cart with a small add-on of CBD gummies to try for on-the-go use. In addition, another pop-up targeted shoppers who explored their pet food section with a promotion discounting their latest CBD dog treats.
Natural Solutions framed these product suggestions to add value to the consumer’s purchase and to be timely and relevant to their interests. Putting customer needs at the center of your marketing efforts is key to creating promotions that convert and messaging that resonates and is seen as helpful, not annoying.
Setup
To set up a cross-sell or upsell promotion in Justuno Basic like Natural Solutions did, follow the steps below.
- Create a new audience rule using the advanced rule set.
- To target shoppers who added a starter kit to their cart, Natural Solutions selected the Cart & Past Order rule condition.
- For items added to the cart during the current session, choose the first condition, Item Added to this Cart THIS visit. If you want to target past cart additions, you can select that, as well.
- You can target cart additions with a variety of parameters including SKU, item name, size, and more.
- Double check that Justuno records the information you want to use as a targeting parameter. You can do this by adding the item you wish to cross-sell to your cart and opening the Justuno tab on your site.
- Select the gear on the left-hand side and select view current session.
- Scroll down to view the items in cart and look for the information you want to use in the rule set.
- Next, add a user engagement rule condition to specify that the visitor they has not closed this pop-up during the current visit. This ensures that visitors who did close the pop-up before won’t be served the same experience again.
- Finally, add in another cart and past order rule condition that states the items currently in their cart do not contain the name of the product you are trying to cross-sell to them. If they already have the gummies in their cart, there’s no reason to serve a product suggestion for more gummies.
The above are the basic conditions when manually creating an upsell or cross-sell promotion, however, you can always add on targeting rules to narrow your audience even further.
Check out the example pop-up below to get inspired, or download the file and add it directly to your Justuno account to get started with your own upselling and cross-selling promotion.

